A few years ago, we migrated email from an "on-premises" Exchange server to Microsoft's cloud email service, Exchange Online (part of their Microsoft 365 suite of SaaS applications, formerly called Office 365). In other words, we decided to stop hosting our email on a single server located in a closet in our office and instead trust Microsoft to take care of all the infrastructure.
There were pros and cons to this, but overall it was a big win - and we've been feeling especially grateful over the last week. Microsoft recently released an emergency patch for the "on-premises" version of Exchange (i.e. the software running our email when it was on the server in the closet). The vulnerability that this patch fixes is a big deal. Up until this emergency patch was released, you were still vulnerable even if you had the most up-to-date version of Exchange with all available updates applied. The common advice going around is that if you have an on-premises Exchange server, configured in a common way, you should just assume that you have been breached. One article claims "at least 30,000 U.S. organizations" have been hacked because of this vulnerability.
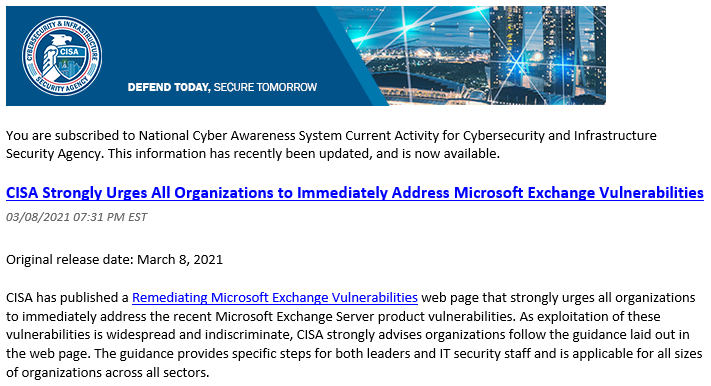
I have received several alerts in the last week (via US-CERT) that essentially scream "if you have an Exchange server patch it right now". Each time I get one of these emails, I have two thoughts:
- I am so glad that this doesn't affect us.
- I feel really bad for the companies that does affect.
Indeed, Exchange Online is unaffected by this - either because it never had this vulnerability or because it was patched immediately by Microsoft.
Here are some things that on-premises Exchange administrators were (and are) working against:
- This was a zero-day vulnerability. Even if your Exchange server was fully up-to-date prior to the emergency patch, you were still vulnerable
- It took Microsoft over a month to notify the public and have an emergency patch ready. In the meantime, China had been actively exploiting this vulnerability. Chinese hackers are still actively exploiting this vulnerability on unpatched Exchange servers.
- Applying emergency patches is not always a simple operation. Sometimes updates and patches might break other things, so you need time to test them. Sometimes a patch or update requires you to have other patches and updates installed before you can apply the new one. This is the case here, and in fact Microsoft later published details on how to remediate the vulnerability if you couldn't immediately apply the emergency patch.
The Cloud™ is not the solution to every problem. Cloud applications can, and do, experience security vulnerabilities and breaches. But in this case, moving to the cloud was a really, really good move for us.