Last week we dealt with a phishing attack that turned out to be a bit scary. The attack used a technique that I knew was possible, but had only read about before (check out this post on Reddit). This was the first time I had actually seen it for myself.
The short story is: this phishing site shows a real Microsoft login page and can give an attacker access to your account even if you use 2FA. This should serve as a reminder of why it is important that humans continue to receive training and education about phishing attacks. I believe that proactive education is the reason that nobody at SEM fell for this attack.
A quick note before moving on: this is not meant to be a technical article. If you're reading this and have any technical suggestions or corrections, feel free to voice them in the comments - just keep in mind that my intended audience is the general public.
A Real Office 365 Login Page
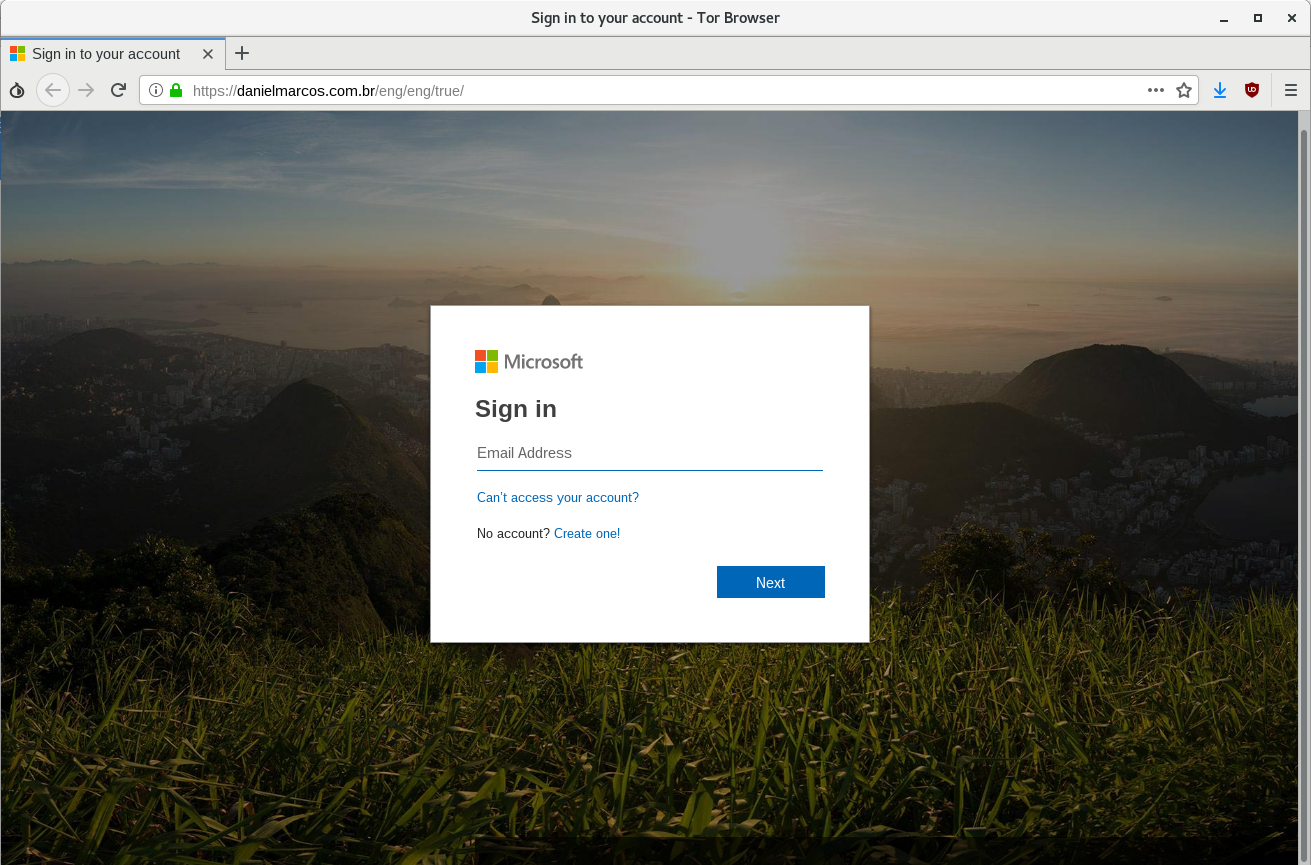
This is the landing page of the phishing attack that we received - if you were to click the link in the phishing email and follow through, you would eventually end up on this webpage. This is definitely a phishing site, but if you're familiar with Office 365 or Outlook on the web, you'll notice that it looks like a very realistic login page. That is because this is a real login page for Microsoft accounts, including Office 365.
If you enter your legitimate email address but mistype your password, you'll be given an "incorrect password" message - this is a real error message from the real login page.
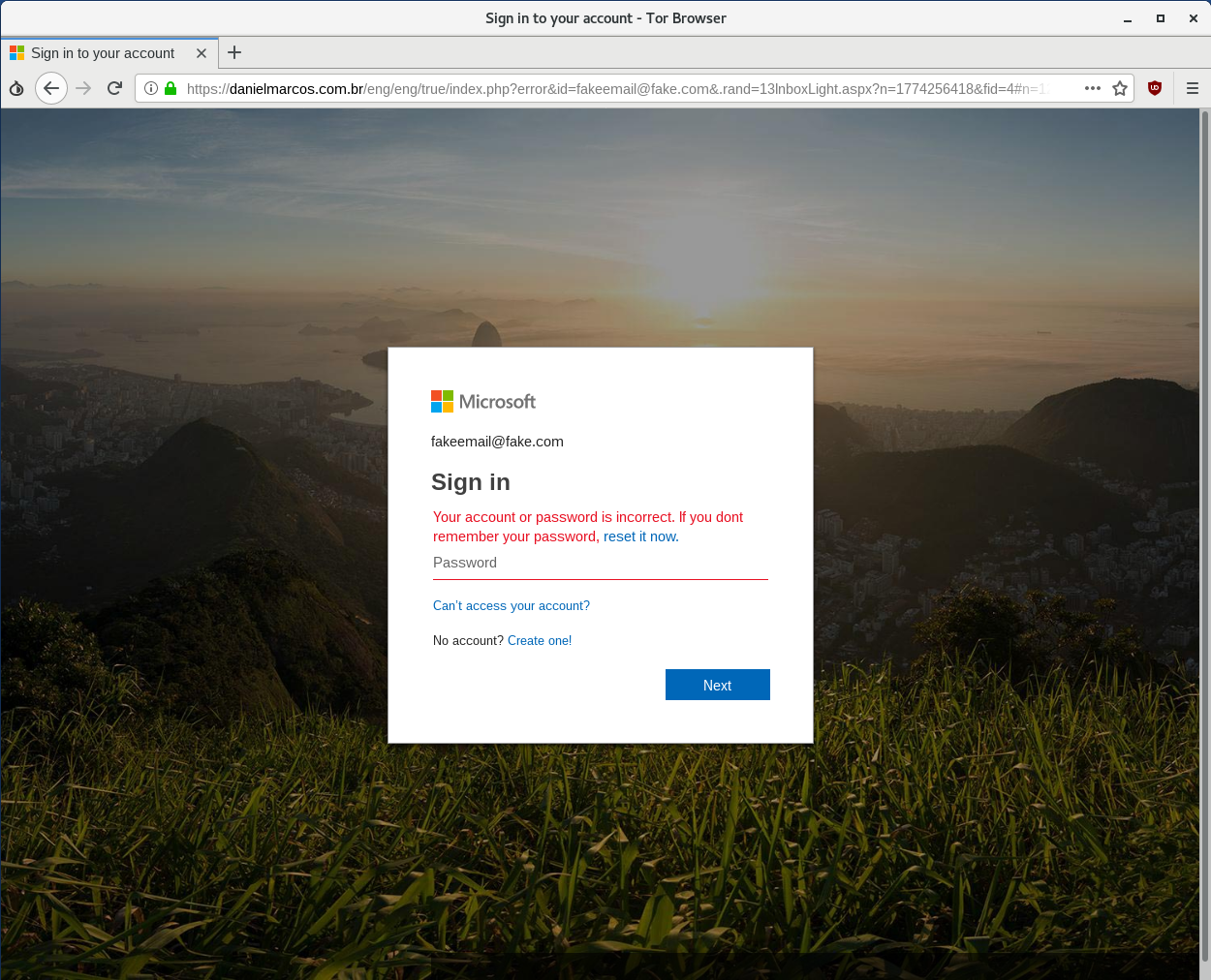
If your company has configured Office 365 to show your logo when employees log in to Office 365, you would see it here too.
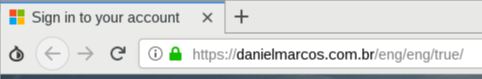
Basically, the phishing server is acting as a middleman between you and the legitimate Office 365 login page. The phishing server will capture anything that you send on this page, and it will also capture anything that Office 365 sends back to you. The only obvious clue that this is fake is the URL.
That's pretty scary by itself, but consider this: most kinds of two-factor authentication do nothing to stop this. The phishing server sees everything you do on this webpage. Think you're safe because your 2FA code expires in 30 seconds, or because it involves a push notification to your phone? Think again. The attacker can simply copy your login session - which was captured by the phishing server when you logged in - and import it into their own browser.
Still don't believe me? Here's a video that demonstrates exactly how this works:
UPDATE: looks like this video is offline now. If it reappears in a different location, I'll update this post.
To be completely clear: two-factor authentication is still a very good thing and you should enable it everywhere that you can. However, there is only one type of 2FA that is actually immune to phishing attacks - check out the "How Secure is your 2FA?" post for more details.
So how can we address this? Two ideas come to mind:
- WebAuthn / FIDO2
- Training and Education
WebAuthn / FIDO2
WebAuthn is a fairly new technology. If you haven't heard of it, maybe you've heard of its predecessor (U2F, which I talk about in the aforementioned blog post on 2FA). WebAuthn is a core component of something called FIDO2, which makes use of a hardware key (like a Yubikey) to authenticate with a website in a way that is immune to phishing attacks, including the kind of attack demonstrated in the video above.
The main problem with FIDO2 is that it is not widely supported yet. If you have a personal Microsoft account you can use it, but support for professional Office 365 accounts only went into public preview a few weeks ago.
You can bet that this is something we are looking into ourselves. It does require a certain amount of technical expertise and again, it is not yet widely supported - off the top of my head, I can't think of any of other services that we use and that natively support WebAuthn/FIDO2.
Training and Education
Education is arguably the single most important part of any cybersecurity program. Humans tend to be the weakest link, and phishing attacks like this exploit human weaknesses.
In the case of this phishing attack, the email came from one of our business partners' employees and also looked pretty realistic. This employee's email had been recently hacked, and the attacker was using it to send phishing emails to other potential victims. Some notable points:
- The email address was 100% legitimate and belonged to someone that we have corresponded with before.
- The subject line looked pretty normal.
- The attachment was named appropriately and even included their company name.
- The email signature was the employee's actual email signature.
However, the contents of the attachment (a PDF) looked like this:
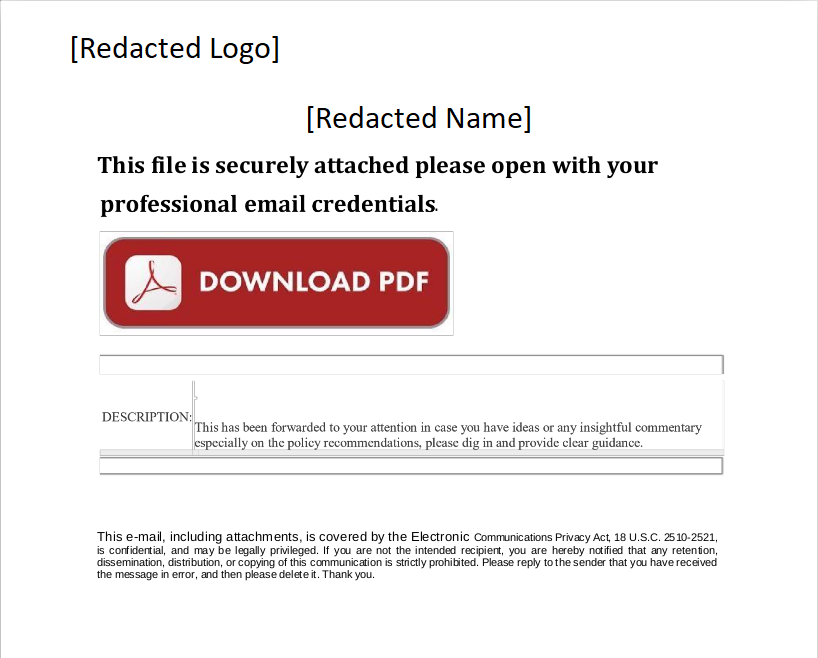
I wish that I could show the unredacted version of this PDF file, because it looks a bit more legitimate - our business partner's real logo and business name were included at the top.
Clearly this is spoofing the whole "click here to open your secure attachment" thing. Despite the real logo and company name, here are some of things that should be cause for concern:
- Legitimate "secure emails" don't normally require you to open a PDF file - usually there is a link right in the email body, or in an attached HTML file.
- The wording is a little strange - e.g. "Please open with your professional email credentials".
- The formatting is off. Look at the block of text next to "DESCRIPTION". Additionally, look at the disclaimer at the bottom - it looks like there are two or three different font sizes there. Legitimate "secure email" messages are usually pretty neat and clean because in order to build trust, they need to look professional.
If you were still unsure, you could ask a coworker or your IT department. Or you could just pick up the phone, call the sender, and ask if they really sent this email. In this scenario, the sender might have answered your phone call like this:
Hey, I am guessing you got the email too? Yeah, it's fake, my email got hacked and our IT department is working on it.
I can say this with confidence because we did call the sender, and they said something very similar. There is nothing wrong with delaying your work for a little while until you know that an email is legitimate.
In this scenario, the attachment should be the farthest anybody gets before figuring out that the whole thing is fake. Even if you made it all the way to the phishing webpage, as shown eaerlier, you should notice that the URL does not correspond to the real Office 365 login page.
The point of explaining all this? Any decent phishing education will teach you to look for these things. Education is what would save you from this kind of phishing attack - because most two-factor authentication won't, and WebAuthn isn't widely available yet.
Looking to get training for you or your employees? There are free resources all over the internet, including SEM's most recent phishing webinar (presented by yours truly):